Eine KI-gestützte App zum Geldverdienen ist jetzt live
Erste Nutzer, die sich Ende April bis Anfang Mai angemeldet haben, konnten bereits zwischen CHF 2’000 und 5’000 verdienen – einige sogar bis zu CHF 12’000.

Technologien wie ChatGPT und Midjourney haben vor kurzem die Welt im Sturm erobert und die Macht der KI demonstriert. Viele Menschen wissen jedoch nicht, dass KI kein neues Konzept ist, sondern sich schon seit Jahren weiterentwickelt hat. Revolutionär ist jetzt, dass jeder Einzelne die KI nutzen kann, um autonom Geld zu verdienen, menschliche Fehler zu vermeiden und ein riesiges Gewinnpotenzial zu erschließen. Genau das bietet Billera – und es funktioniert mühelos, sogar während Sie schlafen.
Der frühe Einstieg zahlt sich aus. Wer bereits im April dabei war, konnte im Mai bis zu CHF 5’000 verdienen. Wer im Mai begann, sieht jetzt Gewinne von bis zu CHF 10’000. Wenn Sie sich jetzt registrieren, haben Sie die Chance, bis Juli CHF 12’000 zu erreichen.
Die drei wichtigsten Vorteile von Billera
Minimaler Aufwand, maximaler Verdienst
Die KI der App arbeitet mit wenig manuellen Eingaben. Einige Benutzer verdienen bereits bis zu CHF 14’750 pro Monat und übertreffen damit die Einnahmen traditioneller Apps, die teure Abonnements erfordern.
Benutzerfreundlich & vollständig automatisiert
Es ist kein technisches Fachwissen erforderlich – die intuitive Benutzeroberfläche macht es für jeden zugänglich. Die KI führt eigenständig Trades aus und kauft und verkauft Vermögenswerte, um die Gewinne zu optimieren.
Schnelle & zuverlässige Abhebungen
Auszahlungen werden innerhalb von 48 Stunden nach Anfrage bearbeitet. Es gibt mehrere Auszahlungsoptionen, darunter Karten, elektronische Geldbörsen und Banküberweisungen.
Wie funktioniert es?
Nachdem Sie einen kleinen Betrag auf Ihr Konto eingezahlt haben, beginnt die KI-Handels-App sofort mit
dem Handel von Währungen, Aktien, Anleihen und Kryptowährungen. Dabei wird auch mit Bitcoin
gehandelt – die bekannteste Kryptowährung, die bereits die Marke von 109.000 US-Dollar
überschritten hat.
Die Transaktionen werden schnell abgeschlossen – manchmal innerhalb von Minuten, nie länger als ein
paar
Stunden.
Die App scannt Tausende von Marktsignalen, von technischen Charts bis hin zu globalen Nachrichten, die sich auf den Wert von Vermögenswerten auswirken, um die besten Trades zum perfekten Zeitpunkt zu bestimmen.
Die wahre Stärke der App liegt in ihrem fortschrittlichen KI-Algorithmus, der große Datenmengen pro Minute verarbeitet und Marktbewegungen mit hoher Genauigkeit vorhersagt, um die Rendite zu maximieren.
Besonders jetzt, in einer Phase außergewöhnlicher wirtschaftlicher Volatilität, entstehen durch starke Schwankungen bei Aktien, Devisen und Kryptowährungen täglich neue Chancen. Genau in diesem Moment bietet Billera einen entscheidenden Vorteil: Die App nutzt diese Marktbewegungen in Echtzeit, um maximale Gewinne zu erzielen – automatisch, rund um die Uhr. Wer heute einsteigt, profitiert von einem Momentum, das in dieser Form nicht lange bestehen bleibt.
Können Sie wirklich von dieser App profitieren?
Billera war zunächst in einer geschlossenen Beta-Phase verfügbar und bis vor zwei Monaten nur begrenzt zugänglich. Die ersten Daten zeigen, dass die Nutzer im Durchschnitt mehr als CHF 14’700 pro Monat verdienen, wobei die Gewinne von der Höhe der Investition und den kontinuierlichen Verbesserungen des Algorithmus abhängen – derzeit liegt die Erfolgsquote bei 92 %.
Unsere Testergebnisse in der realen Welt
Um einen transparenten Beweis zu liefern, haben wir die App 30 Tage lang getestet.
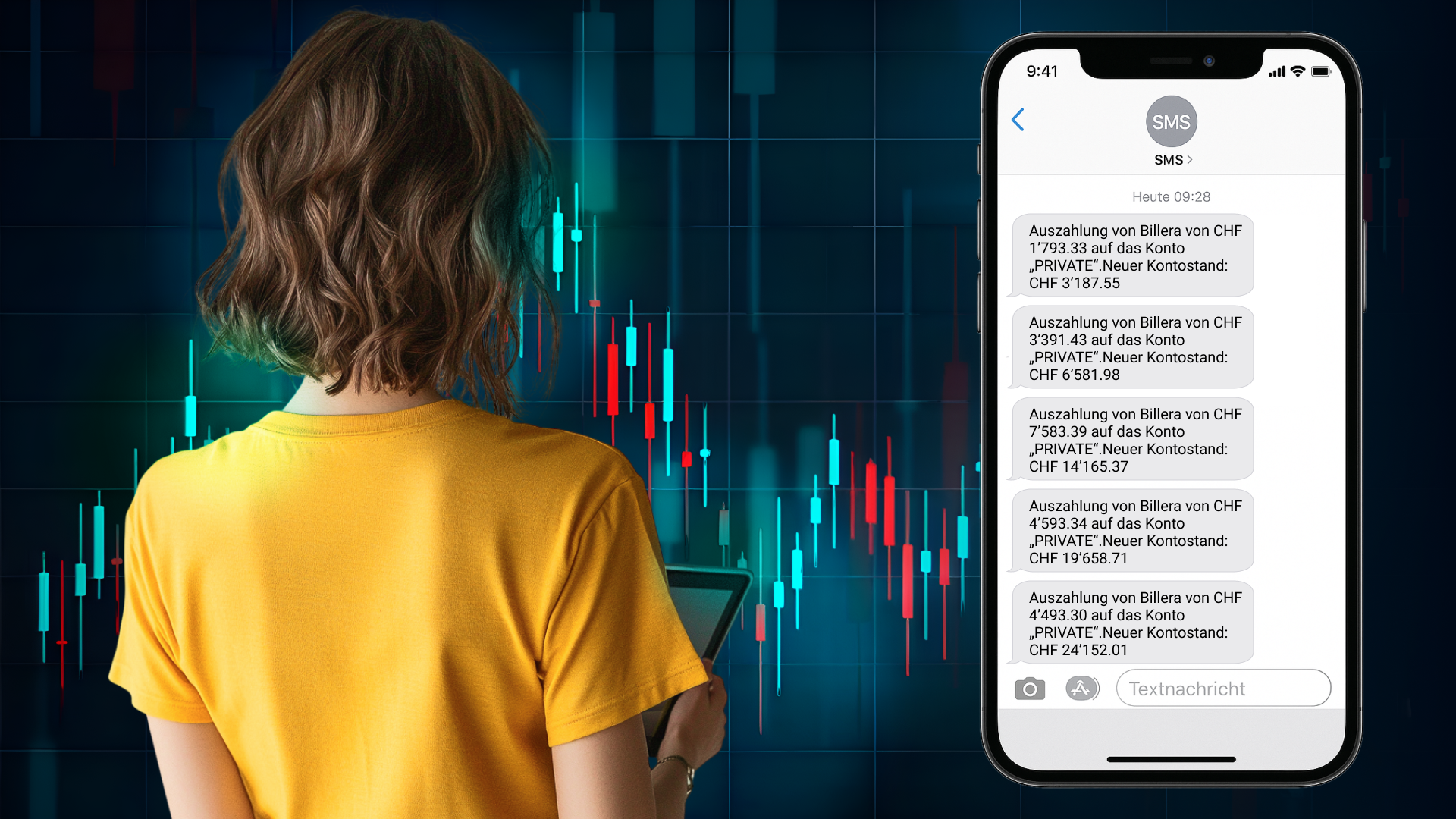
So ist es passiert:
- Nachdem wir uns angemeldet hatten, führte uns ein persönlicher Kundenbetreuer durch die Einrichtung.
- Die KI handelte mit Währungen, Anleihen, Aktien und Kryptowährungen – vier der beliebtesten Instrumente.
- Unsere Erfolgsquote lag bei 73 % und damit auf Augenhöhe mit professionellen Händlern.
- In etwas mehr als einem Monat haben wir einen Gewinn von CHF 24.152,01 erzielt.
Für ein vollautomatisches System, das mit der Zeit immer intelligenter wird, ist das ein beeindruckendes Ergebnis.
Zeitlich begrenzter Zugang – Melden Sie sich jetzt an!
Aufgrund der überwältigenden Nachfrage bieten die Gründer nur während dieser Beta-Phase eine kostenlose Registrierung an. Sobald die Kapazität erreicht ist, müssen neue Nutzer für den Zugang bezahlen.
Wenn Sie bereits im April eingestiegen wären, hätten Sie bis Mai bis zu CHF 5’000 verdienen können. Ein Start im Mai hätte heute bis zu CHF 10’000 gebracht. Melden Sie sich jetzt an, um Ihre Chance nicht zu verpassen – mit etwas Glück sind für Sie bis Juli bis zu CHF 12’000 möglich.
Wie Sie teilnehmen:
1. Beginnen Sie Ihre Reise
Greifen Sie auf die Plattform zu, indem Sie sich über unsere
offizielle Website registrieren, um Ihr Billera-Konto zu erstellen.
2. Verifizieren Sie Ihren Zugang
Nehmen Sie unbedingt den Anruf eines Billera-Beraters entgegen und
aktivieren Sie Ihr Konto. Ohne
diesen Schritt wird der Zugang nicht freigeschaltet – und Ihre Chance ist verloren
3. Starten und optimieren Sie
Sobald Ihr Konto aktiv ist, können Sie mit dem Handel beginnen und Ihre Strategie stetig verfeinern,
um Ihr Verdienstpotenzial zu maximieren.








Ihr Kommentar